Unit 2 - Notes
INT242
Unit 2: Identity and Access Management and Secure Enterprise Network Architecture
This unit focuses on the critical processes of verifying user identity, managing privileges, and designing network infrastructures that resist intrusion while maintaining availability.
1. Authentication (AuthN) and Authorization (AuthZ)
Although often used interchangeably, these are distinct security processes.
Authentication (AuthN)
Definition: The process of verifying the identity of a user, process, or device (verifying "Who are you?").
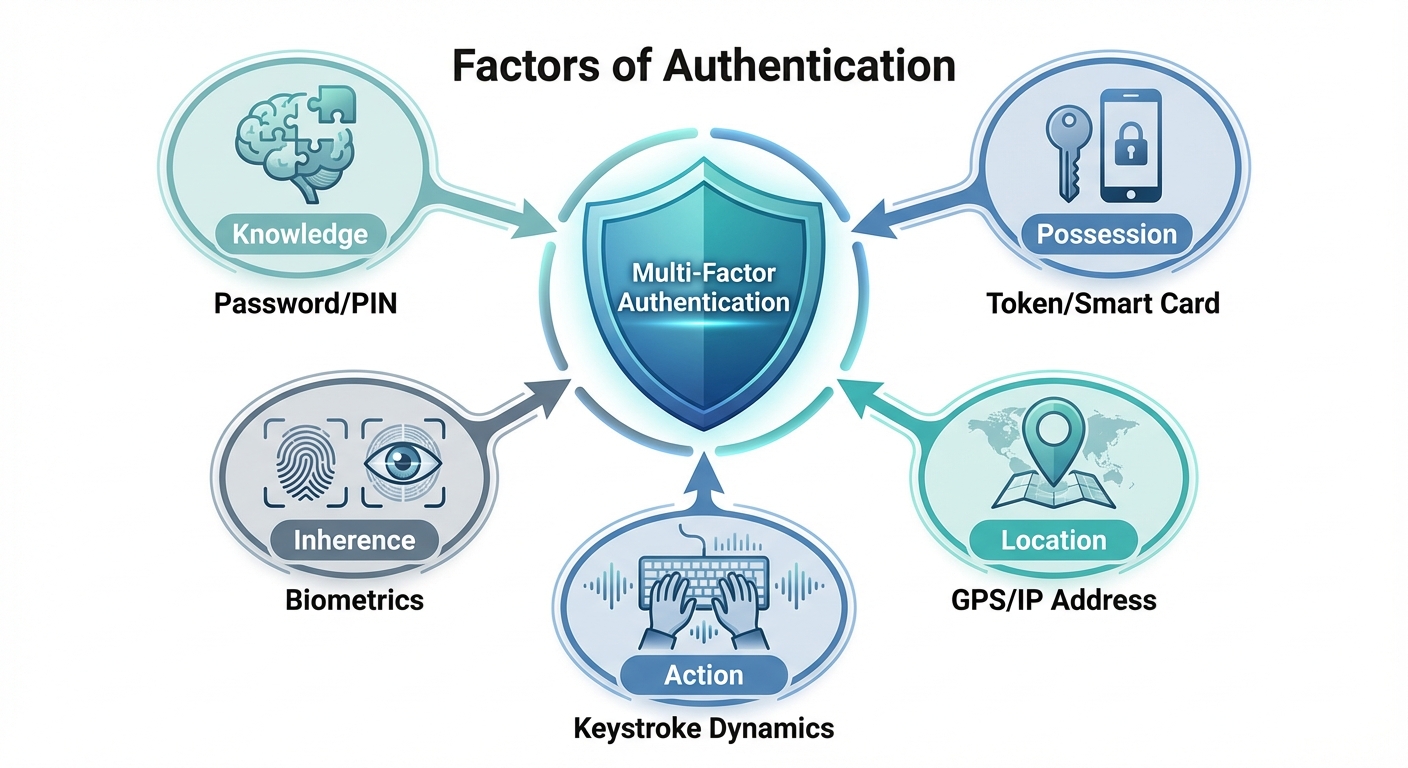
The Factors of Authentication
Multi-Factor Authentication (MFA) requires two or more of the following distinct categories:
- Something you KNOW (Knowledge):
- Passwords, PINs, Pattern swipes.
- Vulnerability: Susceptible to brute force, social engineering, and keyloggers.
- Something you HAVE (Possession):
- Smart cards (CAC/PIV), USB tokens (YubiKey), RSA SecurID fobs, Mobile phones (SMS/Authenticator Apps).
- Vulnerability: Can be stolen or cloned (SIM swapping).
- Something you ARE (Inherence):
- Biometrics: Fingerprint, Retina scan, Iris scan, Facial recognition, Voice print.
- Metrics:
- False Rejection Rate (FRR): Type I error (Legitimate user denied).
- False Acceptance Rate (FAR): Type II error (Imposter allowed).
- Crossover Error Rate (CER): The point where FRR and FAR are equal; lower CER indicates a more accurate system.
- Something you DO (Action/Behavior):
- Keystroke dynamics, gait analysis, signature dynamics.
- Somewhere you ARE (Location):
- GPS geolocation, IP address subnet filtering.
Authorization (AuthZ)
Definition: The process of determining what an authenticated entity is allowed to access or perform (verifying "What can you do?").
Access Control Models
- DAC (Discretionary Access Control):
- The data owner controls access (e.g., Windows NTFS permissions, Unix
chmod). - Flexible but difficult to manage centrally.
- The data owner controls access (e.g., Windows NTFS permissions, Unix
- MAC (Mandatory Access Control):
- Based on security clearance labels (e.g., Top Secret, Secret) and object classification.
- Users cannot change permissions. Used in high-security military/government environments (e.g., SEAndroid, SELinux).
- RBAC (Role-Based Access Control):
- Access is assigned to "Roles" (e.g., Manager, HR, Admin), and users are assigned to Roles.
- Most common in enterprise environments.
- ABAC (Attribute-Based Access Control):
- Context-aware. Decisions based on attributes: User (age, department), Resource (type, sensitivity), and Environment (time of day, location).
- Example: "Managers can access Financial Data only between 9 AM and 5 PM from the office IP."
2. Identity Management (IdM)
Identity Management refers to the lifecycle of a digital identity, ensuring the right people have the right access at the right time.
The IAM Lifecycle
- Provisioning: Creation of the identity, enrollment of credentials, and assignment of initial rights.
- Management/Maintenance: Password resets, updating attributes, modifying roles.
- Authentication/Authorization: The daily verification steps.
- De-provisioning: Disabling accounts immediately upon termination (offboarding) to prevent "orphaned accounts."
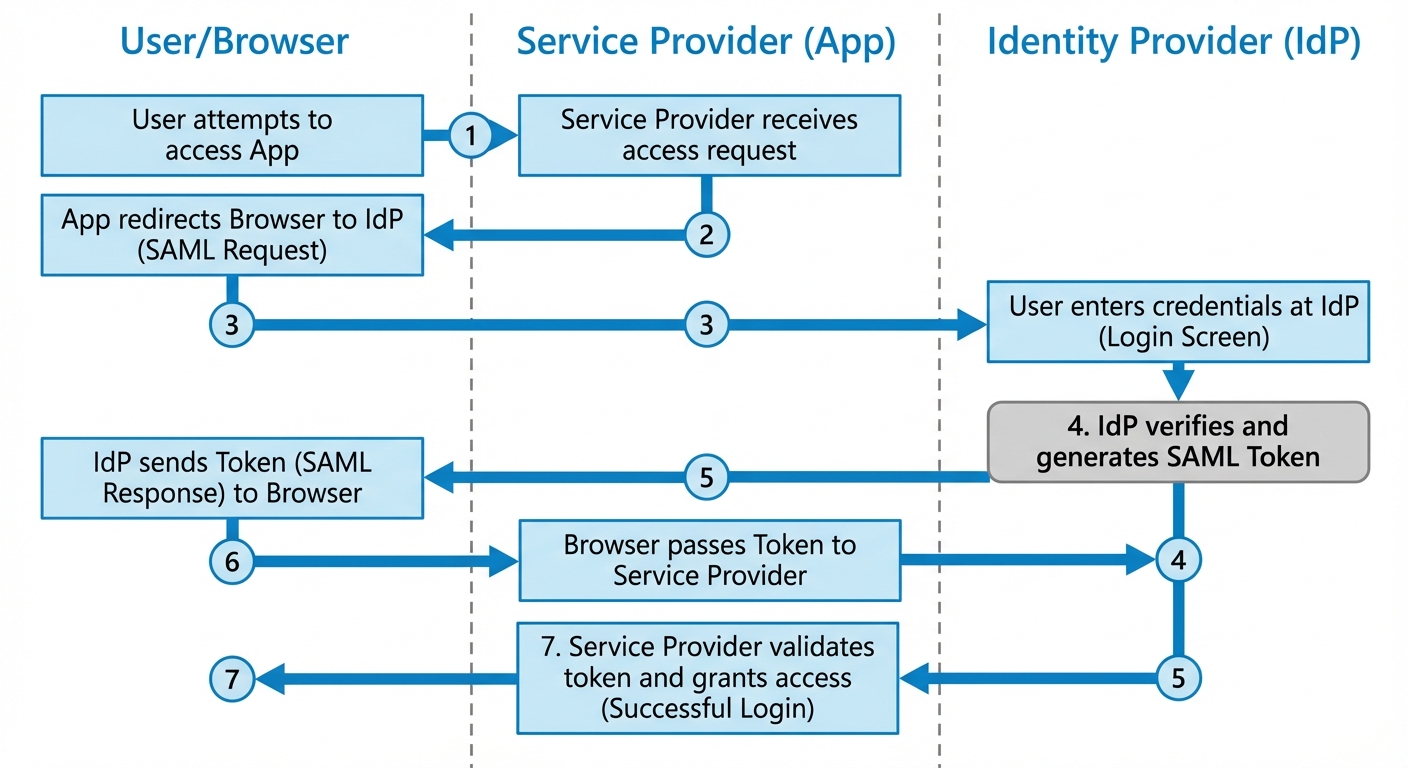
Federation and Single Sign-On (SSO)
SSO allows a user to log in once and access multiple applications without re-entering credentials.
- SAML (Security Assertion Markup Language): XML-based standard for exchanging auth data between an Identity Provider (IdP) and a Service Provider (SP).
- OIDC (OpenID Connect): Built on top of OAuth 2.0; JSON-based identity layer.
- OAuth 2.0: Strictly for authorization (delegated access), not authentication, though often used alongside OIDC.
3. Secure Enterprise Network Architecture
Designing a network topology that segregates traffic based on trust levels.
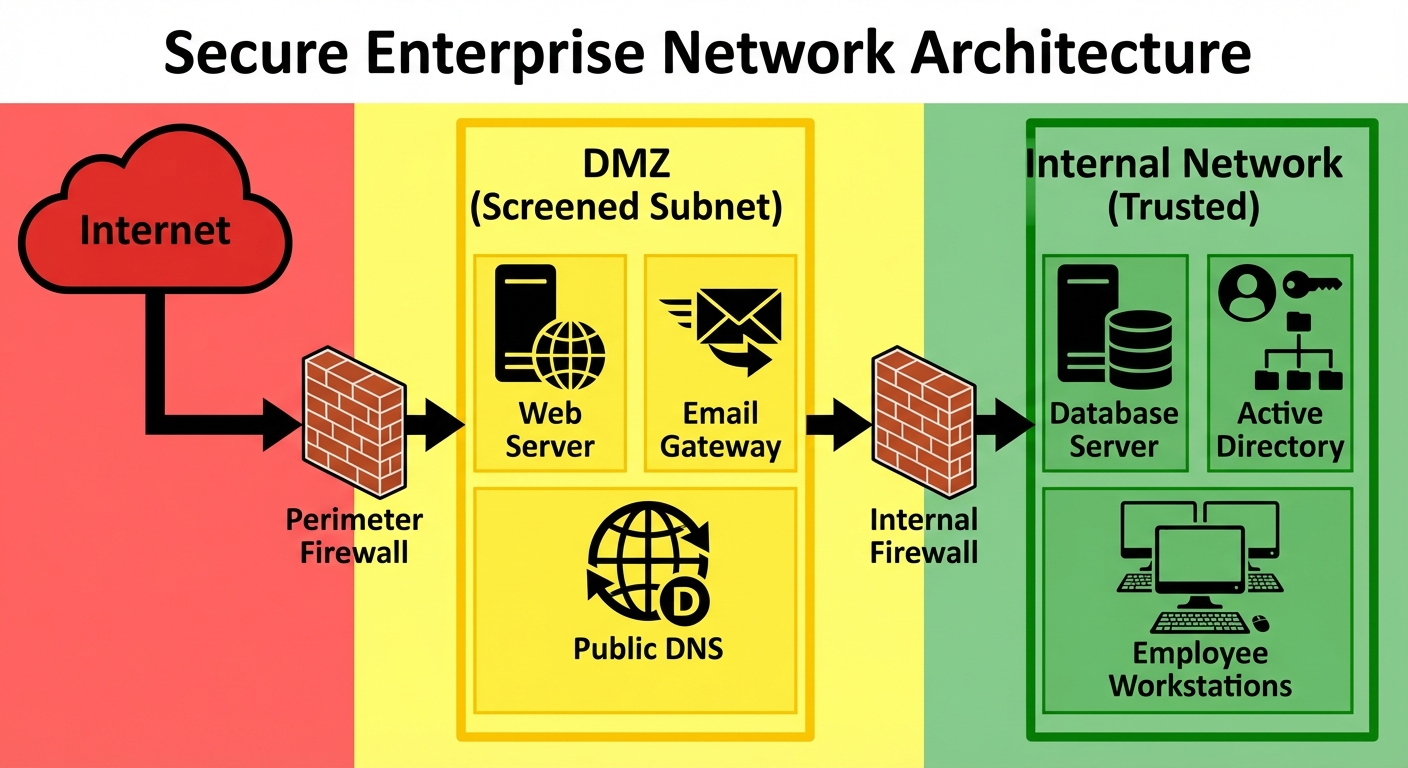
Network Zones
- Untrusted Zone: The Internet.
- DMZ (Demilitarized Zone):
- A buffer zone between the internet and the internal network.
- Hosts public-facing services (Web Servers, SMTP Relays, DNS).
- If a DMZ host is compromised, the internal network remains secure.
- Trusted Zone (Intranet):
- Internal LAN containing sensitive assets (Database servers, Domain Controllers, Workstations).
- No direct access from the Internet.
Network Segmentation
- VLANs (Virtual LANs): Logical separation of a physical switch. Examples: separating VoIP traffic, Guest Wi-Fi, and HR Data into different broadcast domains.
- Air Gapping: Physical isolation of a network from unsecured networks (critical for SCADA/ICS systems).
Zero Trust Architecture (ZTA)
- Philosophy: "Never Trust, Always Verify."
- Assumes the network is already compromised.
- Requires mutual authentication (mTLS) for every internal request, not just at the perimeter.
4. Network Security Appliances
Hardware or software dedicated to protecting the network.
Firewalls
- Packet Filtering (Stateless): Inspects headers (IP, Port) against an Access Control List (ACL). Fast but low security.
- Stateful Inspection: Tracks the state of active connections. Only allows return traffic if it matches an outbound request.
- Next-Generation Firewall (NGFW): Includes Deep Packet Inspection (DPI), Application awareness (blocking "Facebook Games" but allowing "Facebook Chat"), and integrated IPS.
Intrusion Detection & Prevention (IDS/IPS)
- IDS (Detection): Passive monitoring. Alerts on suspicious activity (out-of-band). Does not stop the attack.
- IPS (Prevention): Active inline monitoring. Blocks traffic immediately upon detecting a signature or anomaly.
- NIDS vs. HIDS: Network-based (NIDS) monitors the wire; Host-based (HIDS) monitors a specific server's OS logs and file integrity (e.g., OSSEC).
VPN Concentrators
Manages encrypted tunnels for remote access.
- Site-to-Site: Connects two office branches over the internet.
- Remote Access: Connects a single user (teleworker) to the corporate LAN.
SIEM (Security Information and Event Management)
- Aggregates logs from firewalls, servers, and routers.
- Performs correlation and analytics to detect complex threats.
- Example tools: Splunk, ELK Stack, QRadar.
5. Secure Communications
Protocols ensuring Confidentiality, Integrity, and Authenticity during data transmission.
Cryptographic Protocols
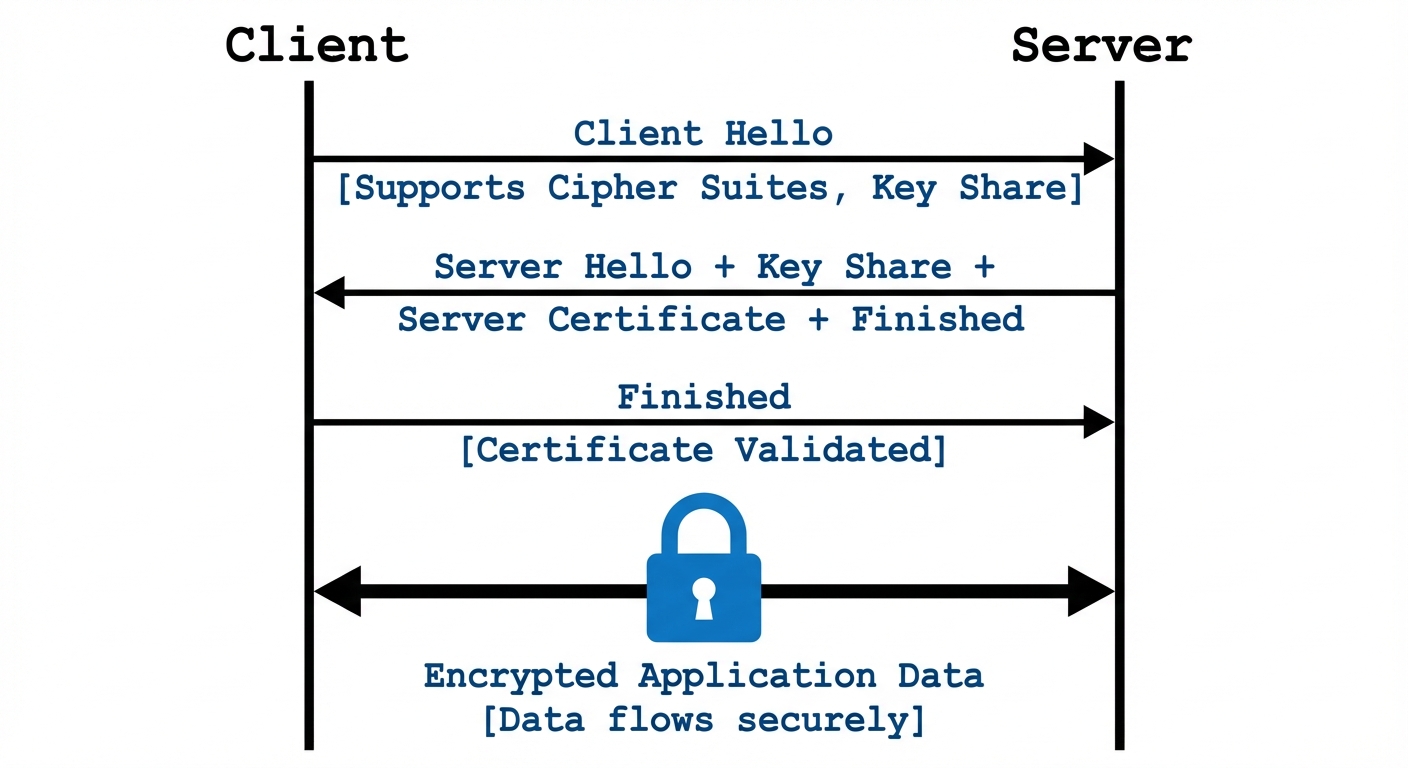
- SSL/TLS (Secure Sockets Layer / Transport Layer Security):
- Encrypts application layer traffic (HTTP becomes HTTPS).
- TLS 1.2 and 1.3 are current standards; SSL is deprecated.
- Uses Asymmetric encryption (Public Key) for the handshake/key exchange and Symmetric encryption for the data session.
- IPsec (Internet Protocol Security):
- Layer 3 security suite for VPNs.
- Transport Mode: Encrypts only the payload (used for host-to-host).
- Tunnel Mode: Encrypts the entire IP packet (header + payload) and wraps it in a new header (used for Site-to-Site VPNs).
Secure Remote Access Protocols
- SSH (Secure Shell) - Port 22:
- Replaces Telnet. Provides encrypted command-line access.
- Supports secure file transfer (SCP/SFTP).
- RDP (Remote Desktop Protocol) - Port 3389:
- Microsoft's GUI remote access. Must be secured with NLA (Network Level Authentication) or tunneled through a VPN.
Code Example: Basic Firewall ACL (Cisco IOS Syntax)
Conceptual example of allowing Web traffic but blocking Telnet.
! Allow traffic from any source to the Web Server on port 80 and 443
access-list 101 permit tcp any host 192.168.1.50 eq 80
access-list 101 permit tcp any host 192.168.1.50 eq 443
! Block Telnet (Port 23) to the Web Server
access-list 101 deny tcp any host 192.168.1.50 eq 23
! Implicit Deny (Invisible rule at the end blocks everything else)
! access-list 101 deny ip any any