Unit 6 - Notes
INT242
Unit 6: Risk Management Processes, Data Protection, and Compliance
1. Risk Management Processes and Concepts
Risk management is the ongoing process of identifying, assessing, and responding to security risks to keep them within an acceptable level. It bridges the gap between technical security measures and business objectives.
Core Terminology
- Asset: Anything of value to the organization (data, hardware, software, people).
- Vulnerability: A weakness or flaw in a system or process that could be exploited (e.g., unpatched software, unlocked door).
- Threat: A potential danger that can exploit a vulnerability (e.g., hackers, earthquake, insider).
- Risk: The probability of a threat exploiting a vulnerability resulting in a negative impact.
- Formula: Risk = Threat × Vulnerability × Impact
- Residual Risk: The risk that remains after security controls have been applied.
- Formula: Total Risk - Controls = Residual Risk
- Risk Appetite: The amount of risk an organization is willing to accept in pursuit of its goals.
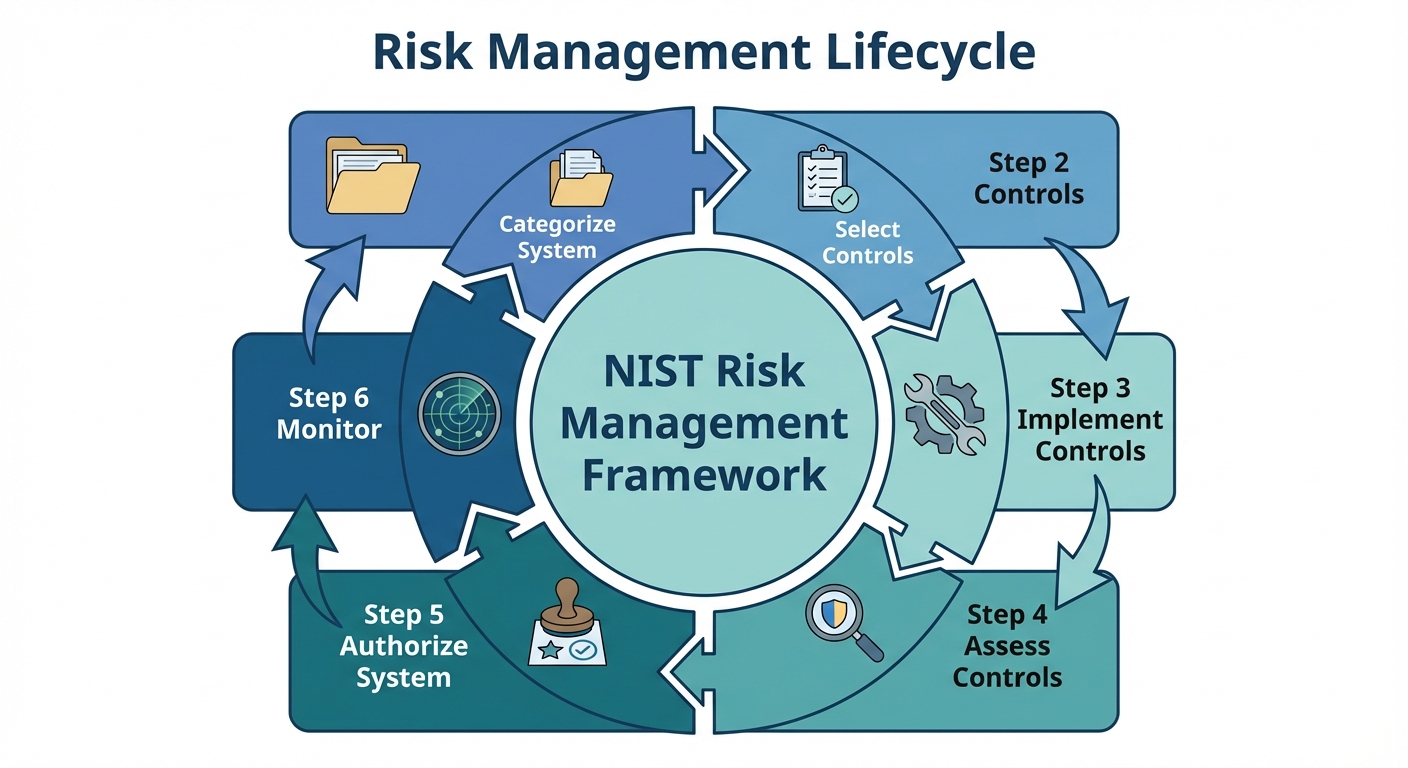
The Risk Management Lifecycle (NIST RMF)
Effective risk management follows a cyclical process:
- Categorize: Define the criticality of the information system.
- Select: Choose appropriate security controls (baseline controls).
- Implement: Deploy the controls.
- Assess: Determine if controls are effective.
- Authorize: Senior management accepts the risk and operates the system.
- Monitor: Continuous monitoring for changes in the threat landscape.
Risk Analysis Methods
- Quantitative Analysis: Assigns concrete financial values to risk. Uses objective data.
- SLE (Single Loss Expectancy): Asset Value (AV) × Exposure Factor (EF). Cost of a single incident.
- ARO (Annualized Rate of Occurrence): How many times per year the incident occurs.
- ALE (Annualized Loss Expectancy): SLE × ARO. The expected yearly cost.
- Qualitative Analysis: Uses subjective ratings (High, Medium, Low) based on expert judgment and probability/impact matrices. Used when concrete data is unavailable.
Risk Response Strategies
Once risk is analyzed, organizations must decide how to handle it:
- Risk Mitigation (Reduction): Implementing controls (firewalls, training) to lower the likelihood or impact.
- Risk Transference (Sharing): Shifting the burden of loss to a third party (e.g., Cyber Insurance, outsourcing).
- Risk Avoidance: Discontinuing the activity that causes the risk (e.g., removing a legacy server).
- Risk Acceptance: Acknowledging the risk and operating without further controls because the cost of mitigation outweighs the potential loss.
2. Vendor Management Concepts (Third-Party Risk)
Supply Chain Risk Management (SCRM) ensures that external partners do not introduce unacceptable risks to the organization.
The Vendor Lifecycle
- Due Diligence (Pre-Contract):
- Assessing the vendor's financial stability and security posture.
- Reviewing SOC 2 reports or ISO certifications.
- Contracting:
- SLA (Service Level Agreement): Defines uptime, performance metrics, and penalties.
- MSA (Master Service Agreement): The overarching legal contract.
- Right to Audit Clause: Allows the client to inspect the vendor’s security.
- Onboarding: granting least-privilege access to vendor accounts.
- Continuous Monitoring: Regular review of vendor performance and security changes.
- Offboarding: Ensuring data destruction and access revocation when the relationship ends.
Key Risks
- Upstream dependencies: Risks from the vendor's own suppliers (4th party risk).
- Data Sovereignty: Understanding where the vendor physically stores data (legal jurisdiction issues).
3. Audits and Assessments
While often used interchangeably, audits and assessments serve different functions in governance.
Security Assessment
- Goal: Improvement.
- Nature: A flexible review of systems to identify vulnerabilities and recommend changes.
- Types:
- Vulnerability Scanning: Automated checks for known flaws.
- Penetration Testing: Simulating a cyberattack to prove exploitability.
Security Audit
- Goal: Compliance and Verification.
- Nature: A formal examination against a specific standard (checklist). Pass/Fail outcome.
- Types:
- Internal Audit: Performed by company staff; report goes to internal management.
- External Audit: Performed by regulatory bodies or independent firms.
- Third-Party Audit: Specifically checking a vendor.
SOC Reports (Service Organization Control)
Critical for vendor management.
- SOC 1: Focuses on financial reporting controls.
- SOC 2: Focuses on the "Trust Services Criteria" (Security, Availability, Processing Integrity, Confidentiality, Privacy).
- Type I: Point-in-time snapshot (Design of controls).
- Type II: Over a period of time (6-12 months) proving operational effectiveness.
- SOC 3: A public, high-level summary of SOC 2 (marketing use).
4. Data Classification and Compliance
Data classification organizes data based on its sensitivity and the impact to the organization if disclosed. This determines the level of security controls required.
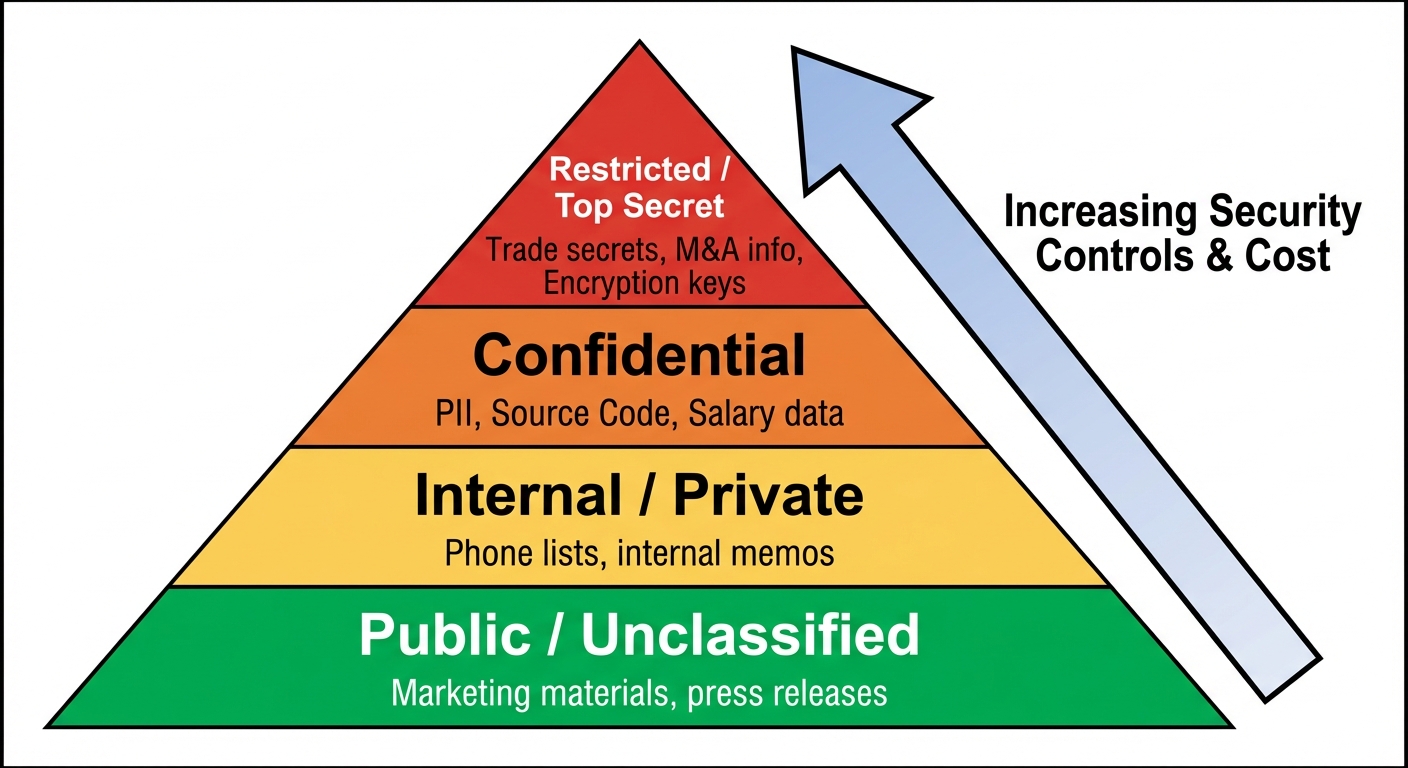
Classification Roles
- Data Owner: Senior management accountable for the data; decides the classification level.
- Data Steward/Custodian: IT staff responsible for the technical implementation (backups, ACLs) based on the Owner's requirements.
- Data Processor: Any entity that processes data on behalf of the controller.
Compliance and Regulatory Frameworks
- GDPR (General Data Protection Regulation): EU regulation.
- Key Concepts: Right to be Forgotten, Data Portability, Data Protection Officer (DPO), heavy fines (4% of global turnover).
- HIPAA (Health Insurance Portability and Accountability Act): US regulation protecting PHI (Protected Health Information).
- PCI-DSS (Payment Card Industry Data Security Standard): Protecting credit card data.
- Requires network segmentation, encryption, and regular scanning.
- CCPA/CPRA: California consumer privacy laws, similar to GDPR.
Data Loss Prevention (DLP)
Technology used to enforce classification policies.
- Network DLP: Scans data in motion (email, web uploads) for keywords/patterns (e.g., SSNs).
- Endpoint DLP: Prevents copying data to USB drives or printing.
- Storage DLP: Scans data at rest to find misclassified files.
5. Personnel Policies
Humans are often the "weakest link" in cybersecurity. Personnel policies mitigate insider threats and human error.
Administrative Controls
- Separation of Duties (SoD): Critical tasks require two or more people to complete so that no single person can commit fraud alone.
- Least Privilege: Users are granted only the minimum access necessary to do their job.
- Job Rotation: Moving employees between roles to detect fraud and reduce burnout/single points of failure.
- Mandatory Vacation: Requiring employees to take time off (1-2 weeks consecutive) allows auditors to review their work for fraud.
- Acceptable Use Policy (AUP): Rules defining how employees can use company equipment (e.g., no illegal downloads, no personal business).
Onboarding and Offboarding
- Background Checks: Screening for criminal history and credit issues (financial pressure creates risk).
- NDAs (Non-Disclosure Agreements): Legal binding to protect trade secrets.
- Termination Procedures:
- Disable account access immediately (simultaneous with notification).
- Exit interview.
- Return of assets (laptops, badges, tokens).
- Escort off premises.
6. Recent Trends in Security Governance and Data Protection
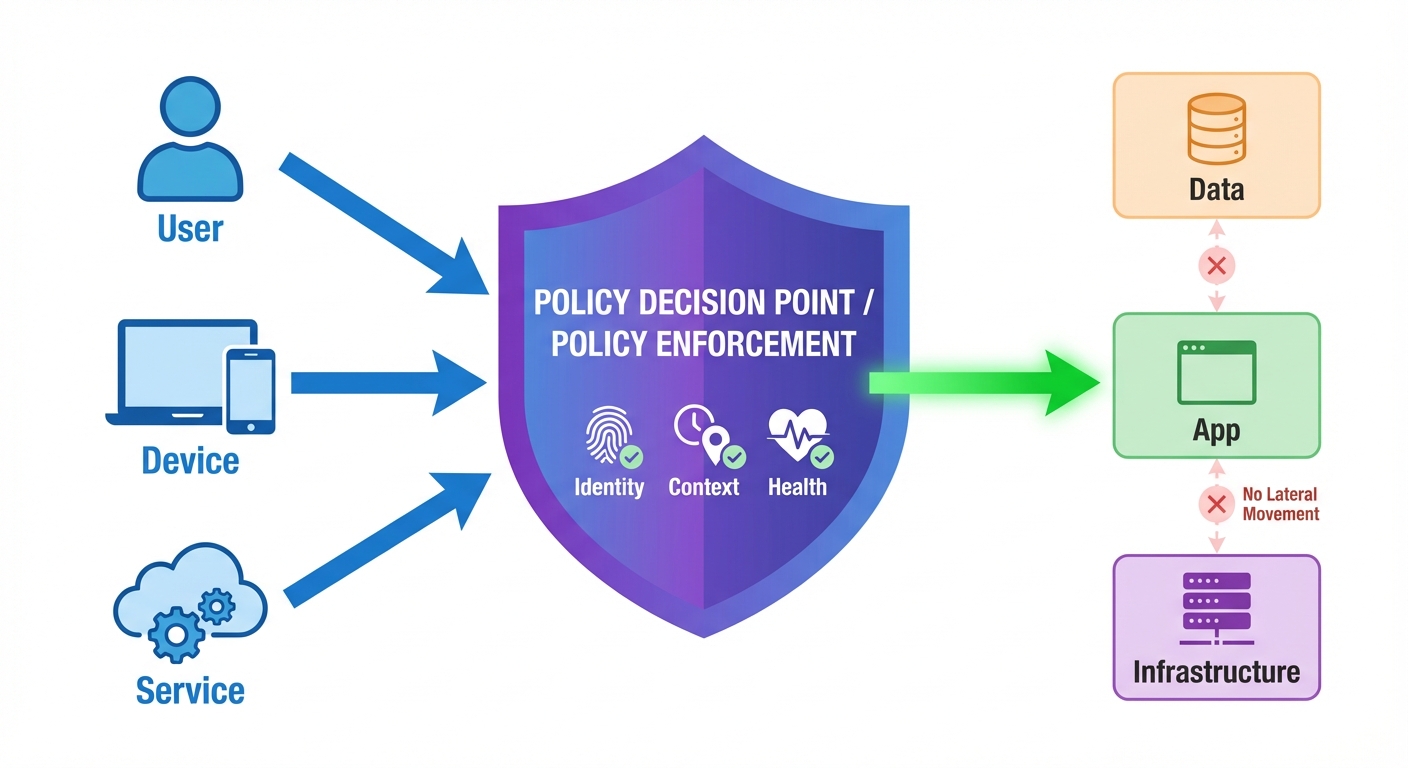
Zero Trust Architecture (ZTA)
The traditional "castle and moat" perimeter model is obsolete. ZTA operates on the principle: "Never Trust, Always Verify."
- Every access request is verified regardless of where it originates (inside or outside the network).
- Relies heavily on Identity and Access Management (IAM) and micro-segmentation.
Privacy by Design (PbD)
Integrating data protection into the development phase of systems, rather than adding it as an afterthought.
- Data Minimization: Only collecting the data strictly necessary for the purpose.
- Pseudonymization: Replacing private identifiers with fake identifiers to reduce risk.
GRC Automation (Governance, Risk, and Compliance)
- Continuous Compliance: Using tools to automatically check cloud environments against standards (e.g., checking AWS against CIS benchmarks daily) rather than annual audits.
- AI in Risk Management: Using machine learning to predict risk scenarios based on global threat intelligence feeds.