Unit 2 - Notes
CSC203
Unit 2: Cryptography Basics
1. Introduction to Cryptography
Cryptography is the science and art of securing information and communication techniques to derive it from mathematical concepts and a set of rule-based calculations called algorithms so that only those for whom the information is intended can understand it.
In the context of Blockchain technology, cryptography is not used to hide information (as the ledger is usually public), but to prove ownership, verify the integrity of transactions, and ensure immutability.
Core Goals of Cryptography
- Confidentiality: Ensuring that information is accessible only to those authorized to have access.
- Integrity: Guaranteeing that the information has not been altered during transmission or storage.
- Authentication: verifying the identity of a user or system.
- Non-repudiation: preventing a user from denying previous actions or commitments (essential for transactions).
Basic Terminology
- Plaintext: The original, readable message or data.
- Ciphertext: The scrambled, unreadable output after encryption.
- Encryption: The process of converting plaintext into ciphertext.
- Decryption: The process of converting ciphertext back into plaintext.
- Key: A piece of information (parameter) that determines the functional output of a cryptographic algorithm.
2. Cryptographic Primitives
Cryptographic primitives are the low-level algorithms and theoretical building blocks used to build cryptographic protocols for computer security systems. They are the fundamental tools used to create the security mechanisms in a blockchain.
A. Cryptographic Hash Functions
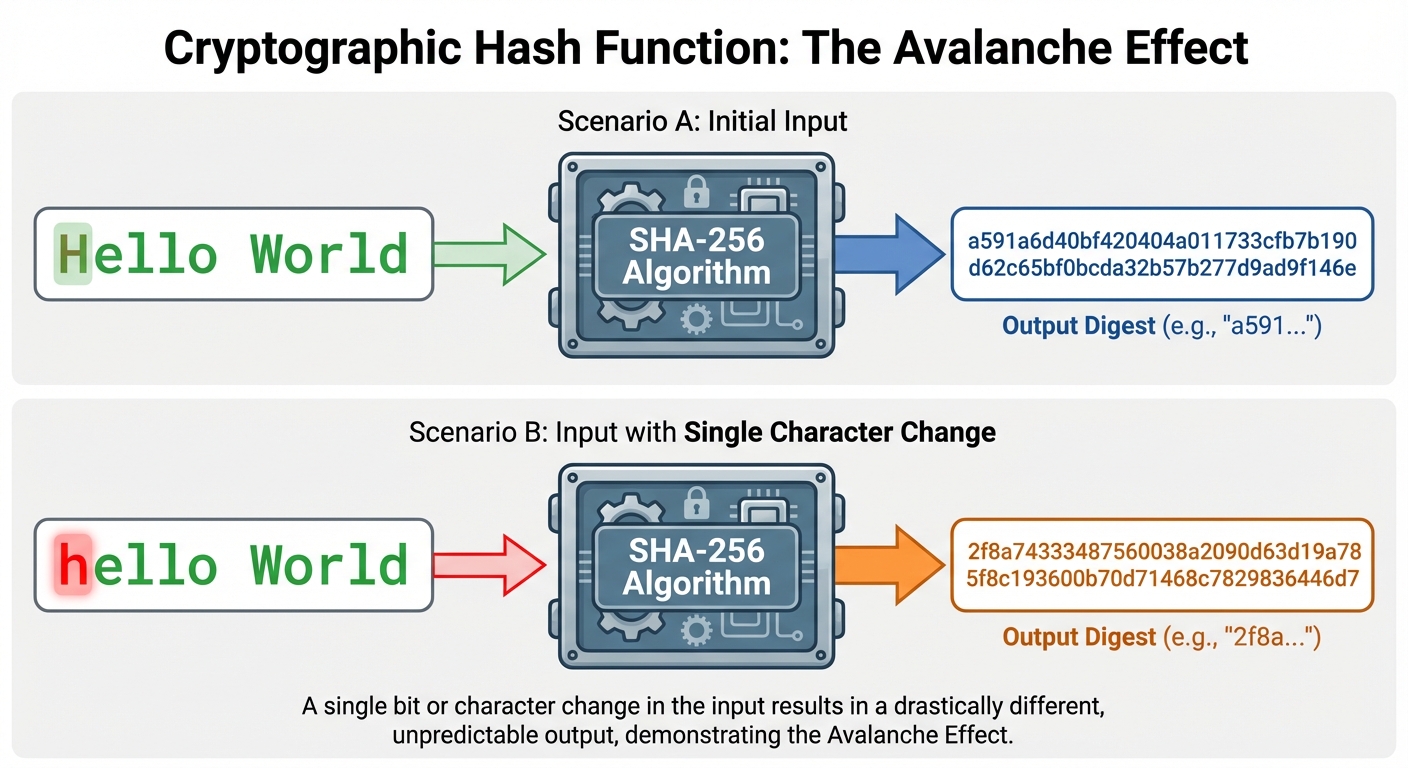
A hash function is a mathematical algorithm that maps data of arbitrary size to a bit array of a fixed size (the "hash" or "digest"). In blockchain, the most common standard is SHA-256 (Secure Hash Algorithm 256-bit).
Key Properties required for Blockchain:
- Deterministic: The same input always produces the exact same output.
- Pre-image Resistance (One-way): It is computationally infeasible to reverse-engineer the input from the output hash.
- Collision Resistance: It is infeasible to find two different inputs that produce the same output hash.
- Avalanche Effect: A tiny change in the input (e.g., flipping one bit) produces a drastically different output hash.
B. Digital Signatures
Digital signatures are primitives that provide authentication, non-repudiation, and integrity. They are the digital equivalent of a handwritten signature but are far more secure.
The Process:
- Signing: The sender generates a hash of the message and encrypts that hash with their Private Key.
- Verification: The receiver decrypts the signature using the sender's Public Key and compares it to a locally generated hash of the message. If they match, the signature is valid.
C. Cryptographically Secure Pseudo-Random Number Generators (CSPRNG)
Used for generating private keys (nonces). Standard random number generators in programming languages are predictable; CSPRNGs utilize high-entropy sources to ensure keys cannot be guessed.
3. Symmetric Cryptography
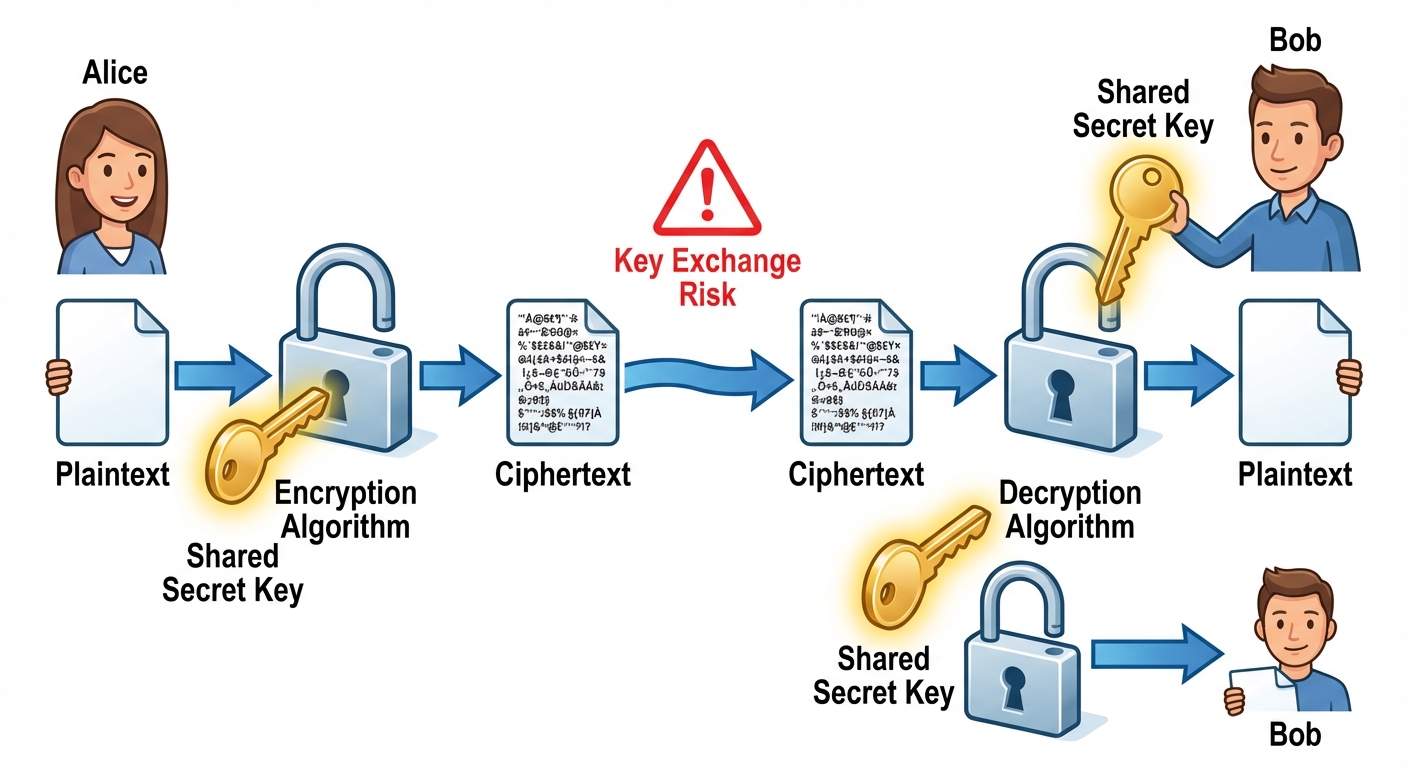
Symmetric Cryptography (also known as Secret-Key Cryptography) is a system where the same key is used for both encryption and decryption.
Mechanism
The sender and the receiver must share a common secret key.
Characteristics
- Speed: Symmetric algorithms are generally very fast and computationally efficient.
- Usage: Best suited for bulk data encryption (e.g., encrypting a local database or a file).
- Common Algorithms: AES (Advanced Encryption Standard), DES (Data Encryption Standard - obsolete), 3DES.
The Key Distribution Problem
The major weakness of symmetric cryptography is the Key Distribution Problem. How do two parties share the secret key securely without a third party intercepting it? If the key is intercepted during transmission, the entire system is compromised.
4. Asymmetric Cryptography (Public-Key Cryptography)
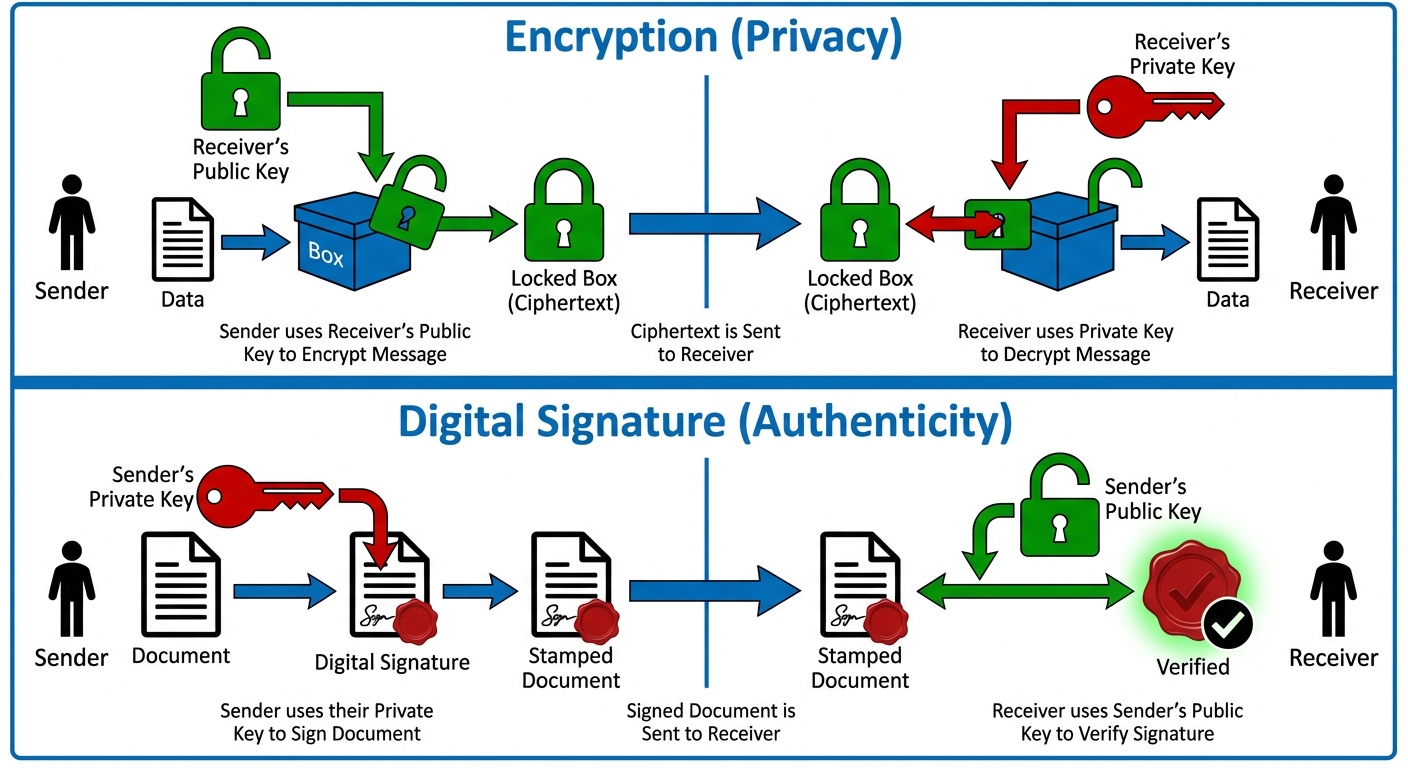
Asymmetric Cryptography solves the key distribution problem by using a pair of mathematically related keys:
- Public Key: Can be shared openly with anyone (acts like a bank account number or email address).
- Private Key: Must be kept secret by the owner (acts like a password or PIN).
How it Works
The keys work in pairs. Whatever is encrypted with one key from the pair can only be decrypted by the other key from that same pair.
Two Main Use Cases
A. Encryption for Confidentiality
- Goal: Send a private message to Bob.
- Action: Alice encrypts the message using Bob's Public Key.
- Result: Only Bob can decrypt it because only Bob has the corresponding Private Key.
B. Digital Signatures (Critical for Blockchain)
- Goal: Prove that Alice created the transaction.
- Action: Alice signs the transaction hash using Alice's Private Key.
- Result: Anyone can verify the signature using Alice's Public Key. If it works, it proves Alice owns the private key without her ever revealing it.
Common Asymmetric Algorithms in Blockchain
- RSA (Rivest–Shamir–Adleman): Relies on the computational difficulty of factoring large prime numbers.
- ECC (Elliptic Curve Cryptography): Used in Bitcoin (secp256k1) and Ethereum. ECC provides the same level of security as RSA but with much smaller key sizes, making it more efficient for blockchain storage and computation.
Comparison: Symmetric vs. Asymmetric
| Feature | Symmetric Cryptography | Asymmetric Cryptography |
|---|---|---|
| Keys | One shared secret key | Key pair (Public & Private) |
| Speed | Very Fast | Slow (computationally heavy) |
| Key Exchange | Difficult (needs secure channel) | Easy (Public key is public) |
| Primary Use | Bulk data encryption | Key exchange, Digital Signatures |
| Blockchain Use | P2P connection encryption | Transaction signing, Wallet addresses |
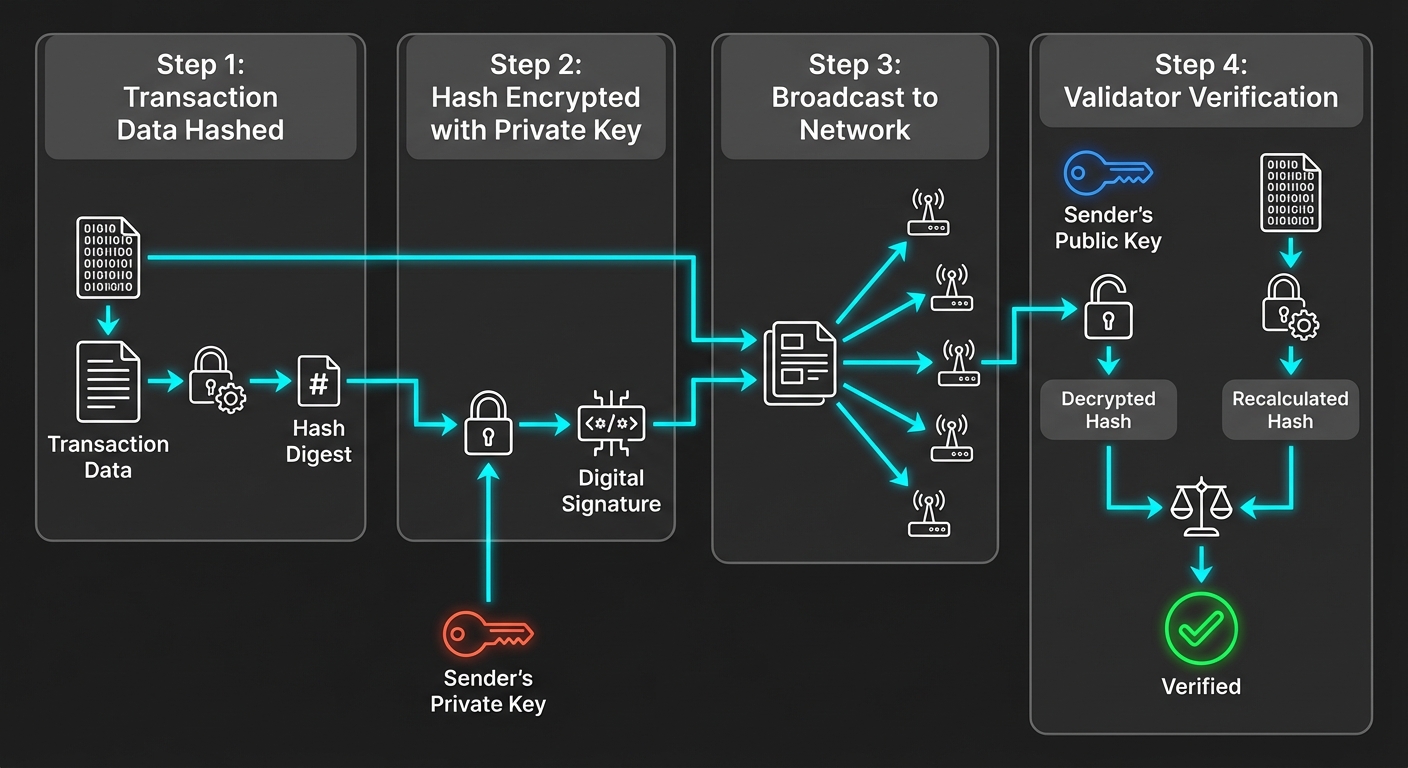
5. Summary of Cryptography Flow in a Blockchain Transaction
To understand how these concepts combine in a practical blockchain scenario (like Bitcoin), consider the flow of a standard transaction.
- Wallet Creation: The user generates a Private Key (via CSPRNG) and derives a Public Key (via ECC). The Public Key is hashed to create the Wallet Address.
- Transaction Initiation: The user creates a transaction (Plaintext) indicating they want to move funds.
- Hashing: The transaction data is passed through a Hash Function (SHA-256) to create a unique Transaction ID (Digest).
- Signing: The user encrypts the Transaction Hash with their Private Key. This creates the Digital Signature.
- Broadcast: The original data and the Digital Signature are broadcast to the network.
- Verification: Nodes (miners) take the original data, hash it themselves, and simultaneously decrypt the attached signature using the user's Public Key.
- Validation: If the node's hash matches the decrypted signature hash, the transaction is valid.