Unit 6 - Notes
MTH401
5 min read
Unit 6: Number theory and its application in cryptography
1. Divisibility and Modular Arithmetic
Divisibility
Let and be integers with .
- Definition: We say divides (denoted ) if there exists an integer such that .
- Properties:
- Reflexive: .
- Transitive: If and , then .
- Linearity: If and , then for any integers .
The Division Algorithm
For any integer and positive integer , there exist unique integers (quotient) and (remainder) such that:
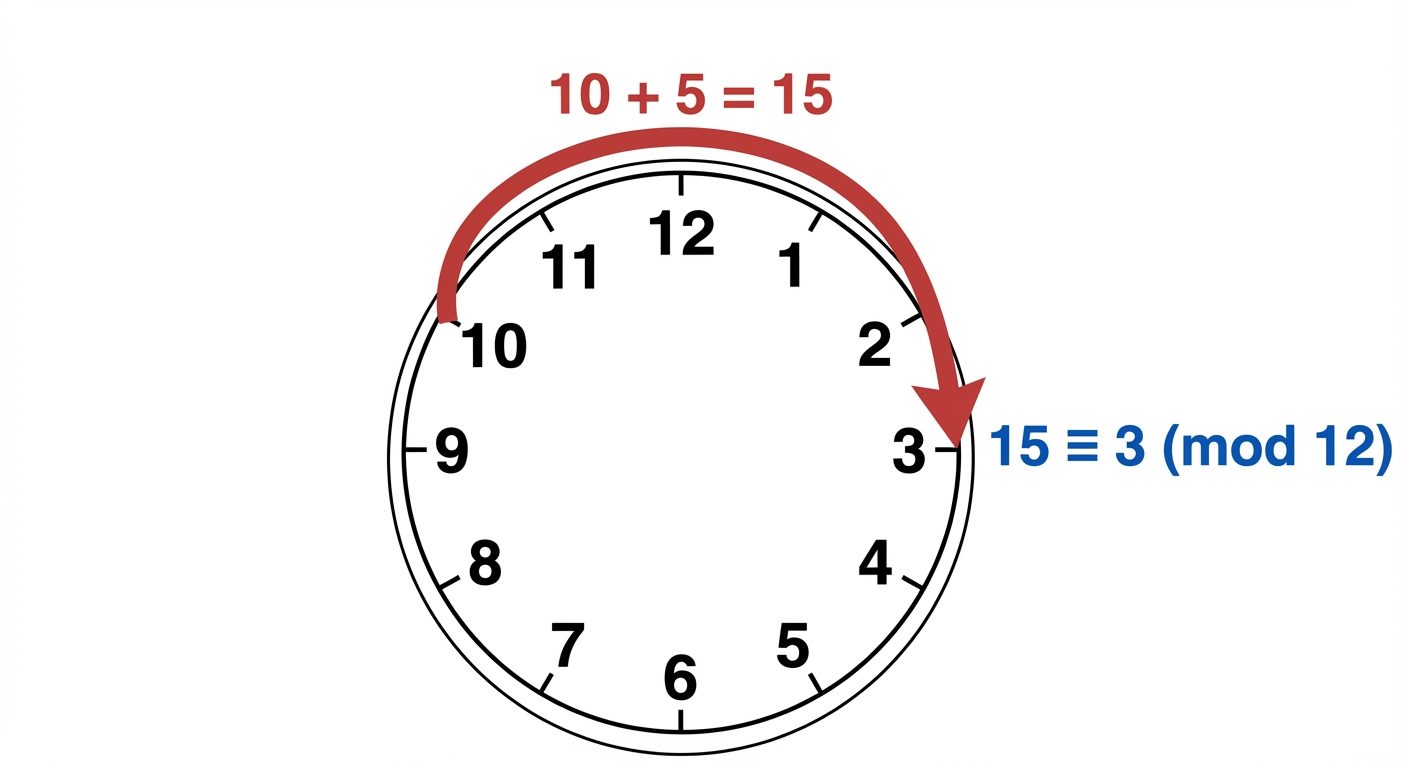
Modular Arithmetic
- Definition: is congruent to modulo () if divides .
- Alternatively, (they have the same remainder when divided by ).
- Arithmetic Operations:
2. Primes, GCD, and LCM
Prime Numbers
- Prime: An integer whose only positive divisors are $1$ and .
- Composite: An integer that is not prime.
- Fundamental Theorem of Arithmetic: Every integer can be written uniquely as a product of primes (up to the order of factors).
Greatest Common Divisor (GCD)
- The largest integer such that and .
- Notation: .
- Coprime: If , and are relatively prime.
Least Common Multiple (LCM)
- The smallest positive integer that is a multiple of both and .
- Relationship: .
3. Euclidean Algorithm and Bezout's Lemma
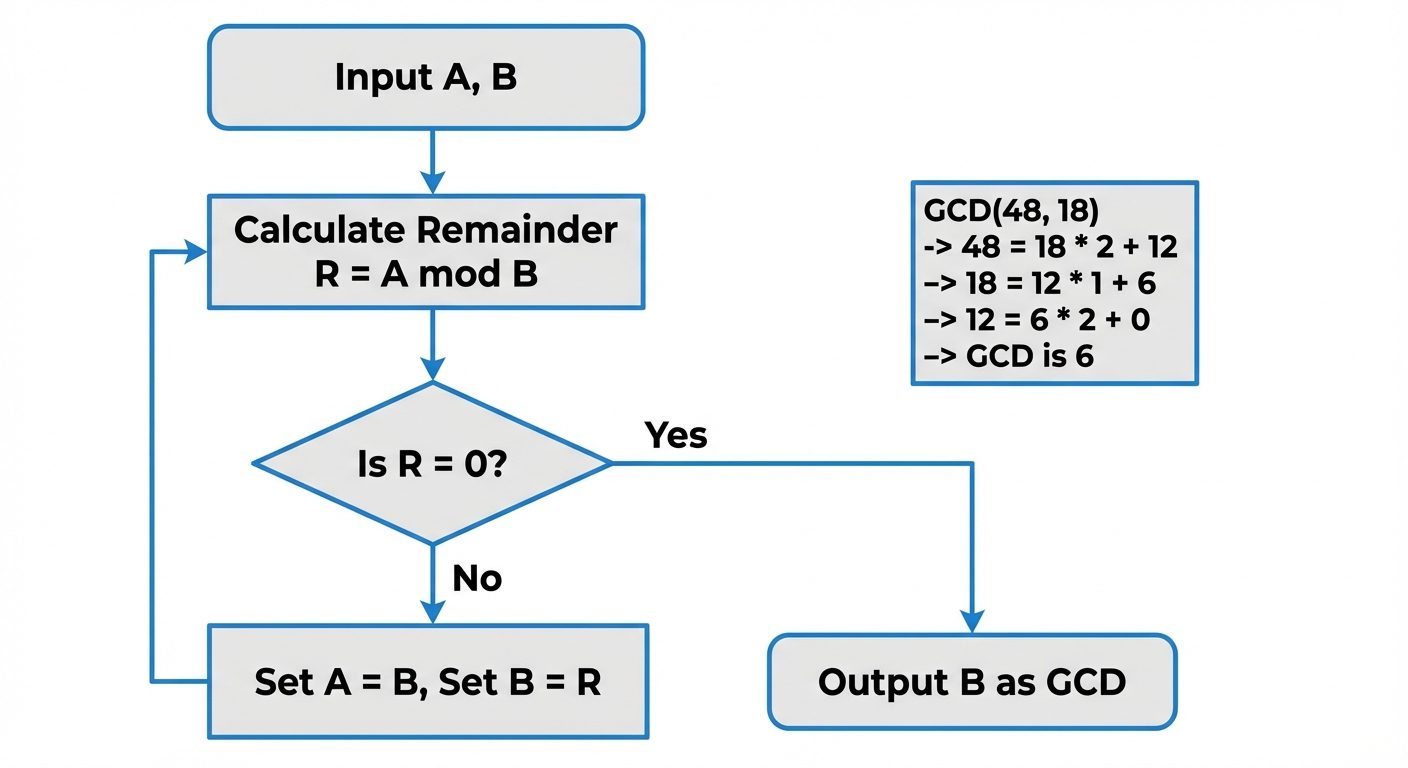
Euclidean Algorithm
An efficient method for computing without factoring. It uses successive divisions:
- Let
- Let
- Let
- Continue until the remainder is 0. The last non-zero remainder is the GCD.
Bezout's Lemma
- For any non-zero integers and , there exist integers and such that:
- and are called Bezout coefficients and can be found using the Extended Euclidean Algorithm (working backward through the Euclidean algorithm steps).
4. Linear Congruence and Inverses
Linear Congruence
- An equation of the form .
- Solvability: A solution exists if and only if , where .
- If solvable, there are exactly distinct solutions modulo .
Inverse of Modulo
- The modular multiplicative inverse of is an integer such that:
- Existence: The inverse exists if and only if (i.e., and are coprime).
- Typically denoted as .
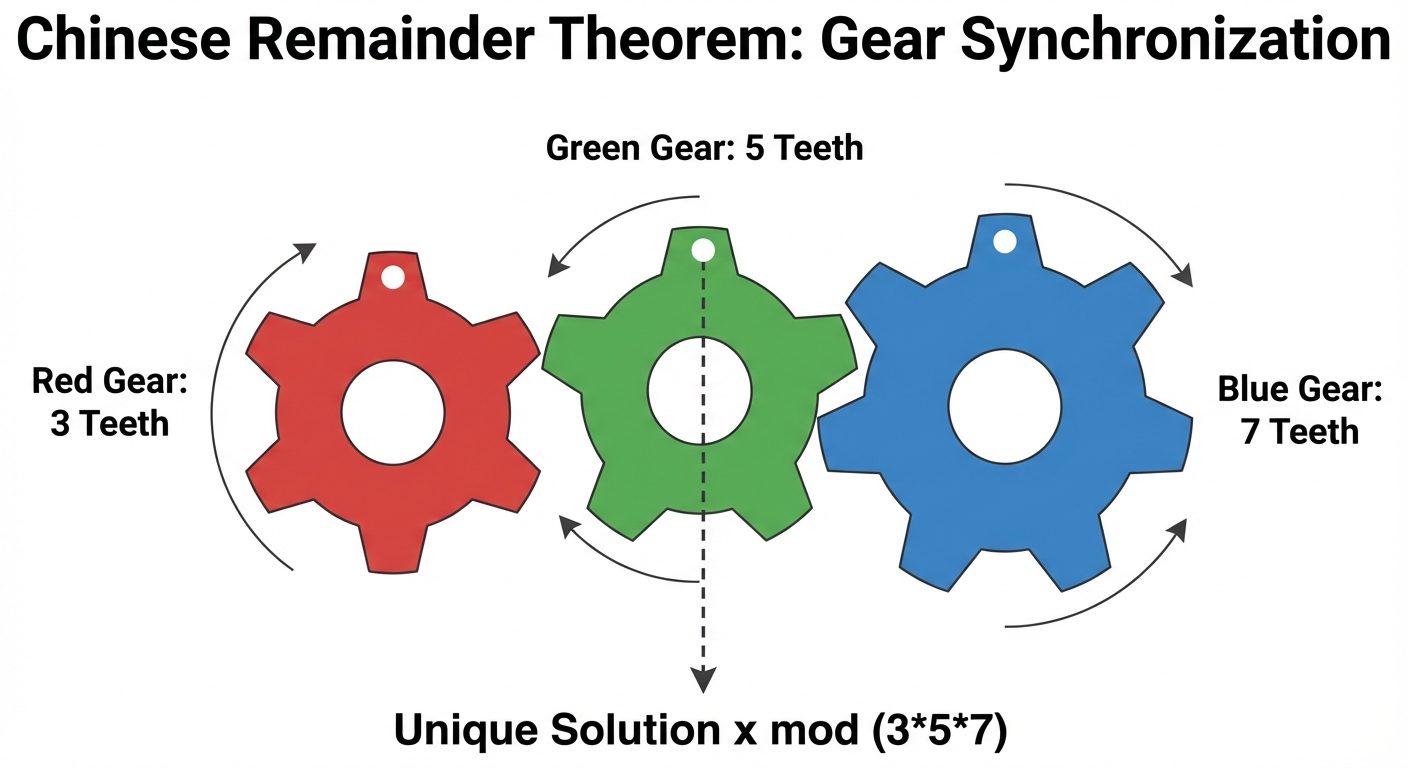
5. Chinese Remainder Theorem (CRT)
- Problem: Solving a system of simultaneous congruences:
- Theorem: If the moduli are pairwise relatively prime (gcd of any pair is 1), then there exists a unique solution for modulo .
- Formula:
- Where
- is the modular inverse of modulo .
6. Fermat’s Little Theorem
- Statement: If is a prime number and is an integer not divisible by :
- Alternative Form: For any integer and prime :
- Application: Crucial for simplifying large exponents in modular arithmetic and serves as the basis for primality testing.
7. Cryptography Applications
Basic Terminology
- Plaintext (): Original message.
- Ciphertext (): Encrypted message.
- Key (): Secret information used for encryption/decryption.
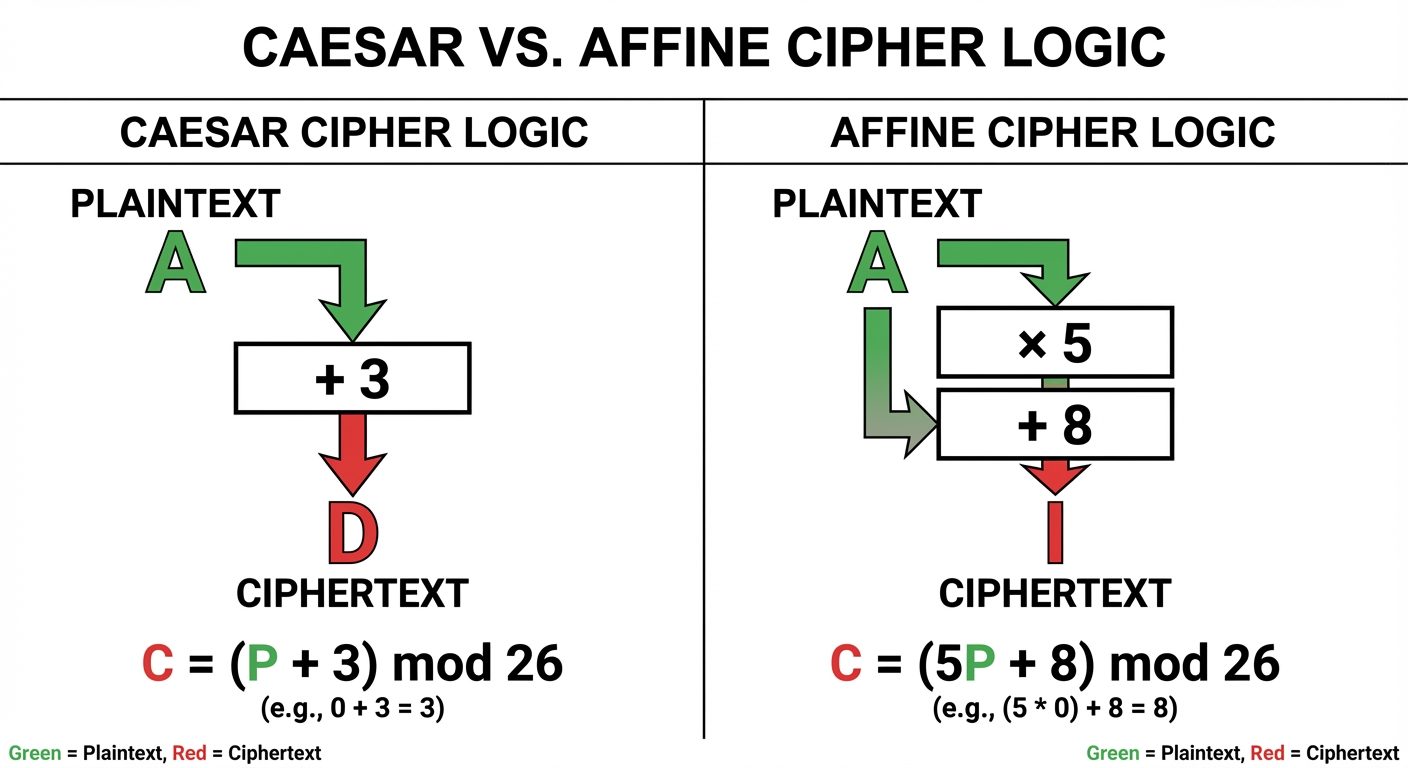
Caesar Cipher
- Type: Shift Cipher (Substitution).
- Encryption: Replace each letter with the letter positions down the alphabet.
(Mapping ) - Decryption:
Affine Transformation (Affine Cipher)
- Encryption Function:
- : Multiplicative key (must be coprime to 26).
- : Additive shift key.
- Decryption Function:
- Requires finding the modular inverse .
- Security: Stronger than Caesar cipher but still vulnerable to frequency analysis.